Basic Permissions
CloudBase provides a multi-level data permission management mechanism to ensure data security while meeting the permission control requirements of different business scenarios.
The database uses the _openid field as the data ownership determination basis when performing read and write operations
Configuration Method
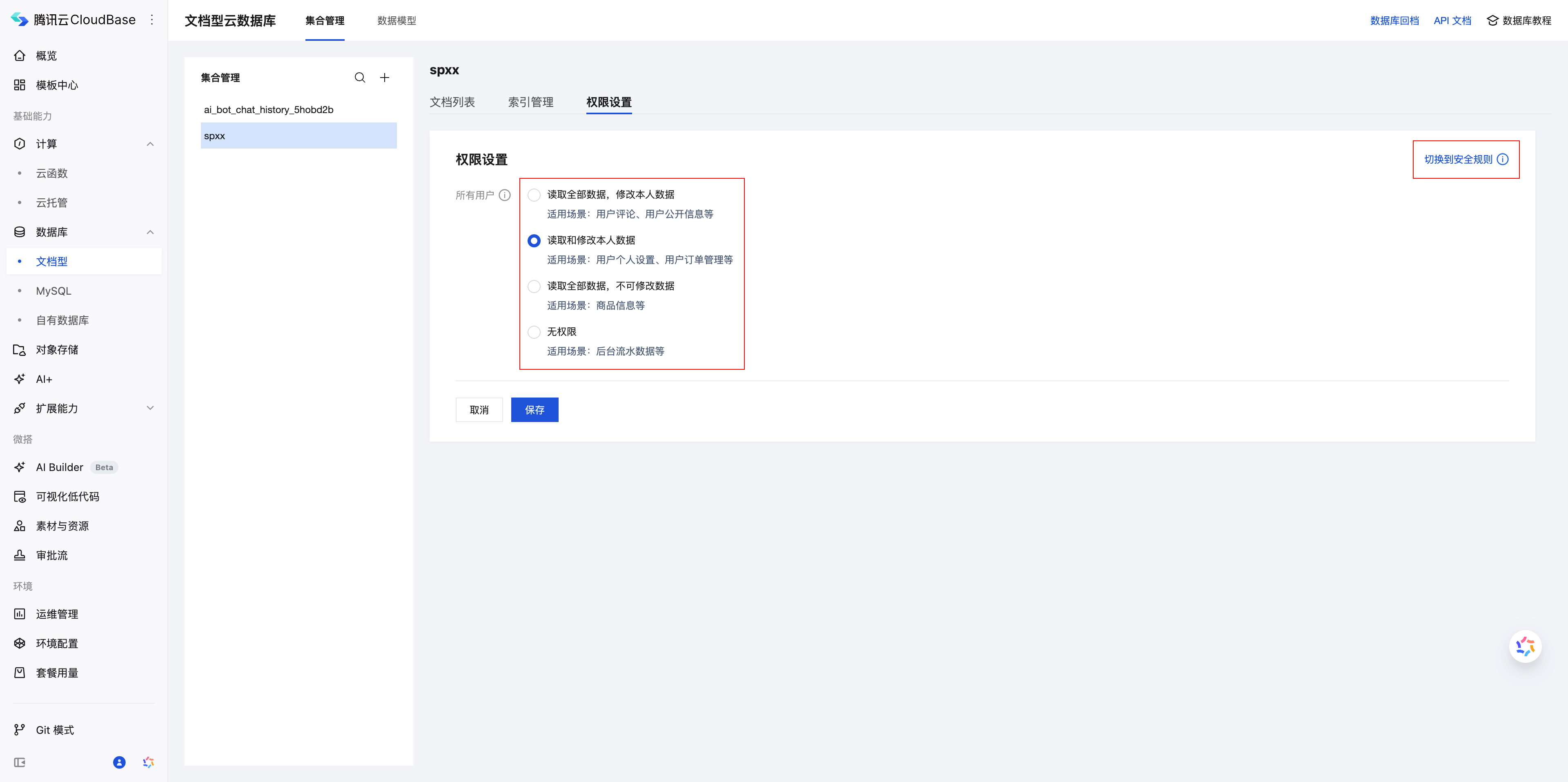
On the CloudBase Console/Document Database/Collection Management page, set corresponding permissions for each collection
Basic permission control provides four preset permission types. Choose according to user identity and data characteristics:
| Permission Type | Use Case | Usage Recommendation |
|---|---|---|
| Read all data, modify own data | Public content like articles, products | Suitable for content display applications |
| Read and modify own data | Private data like user profiles | Suitable for personal information management |
| Read all data, cannot modify data | Configuration data like system settings | Suitable for read-only configuration and reference data |
| No permission | Sensitive data like financial information | Suitable for sensitive data that needs server-side processing |
Security Rules Permissions
Security rules permissions are the document-level permission control capability provided by CloudBase database, offering higher flexibility and precision compared to basic permission control.
For details, please refer to Database Security Rules Explained