get-started
Basic Usage
Security Rules provide robust, fully customizable protection for data in databases and cloud storage. Follow the steps in this guide to easily get started with rules, ensure data security, and protect your application from malicious users.
Preparation: Understanding the Security Rules Language
The Security Rules language uses a JSON structure where key represents the operation type, and value specifies the conditions for allowing operations. The value can be a boolean or an expression string. The expression string syntax resembles Javascript, consisting of either a single logical expression or multiple logical expressions combined using AND/OR operators. When evaluated, the expression determines whether the operation is permitted.
1. Defining Rules and Data Structures
Security rules provide internal variables to obtain the content of request data for access control based on the data. The organization of data may affect how rules are written. For example, in a forum application, all logged-in users are allowed to browse content, but users can only modify or delete their own posts. Therefore, records in the posts collection need to store userID to indicate ownership. Security rules restrict update and delete behaviors based on the userID field, while allowing read behaviors for all logged-in users.
2. Obtaining Security Rules
To use/view existing security rules, log in to the Cloud Development Console, select the desired environment, go to the Database Collection Permission Control page or Cloud Storage Permission Control page, where you can choose to use advanced permission control or view existing security rules already in use.
- Take database collection permission management as an example. Go to the console, select the corresponding environment, and view the details of database collections under that environment.
- On the details page, switch to the Permission Settings tab where you can select to switch from Basic Permission Control to Security Rules.
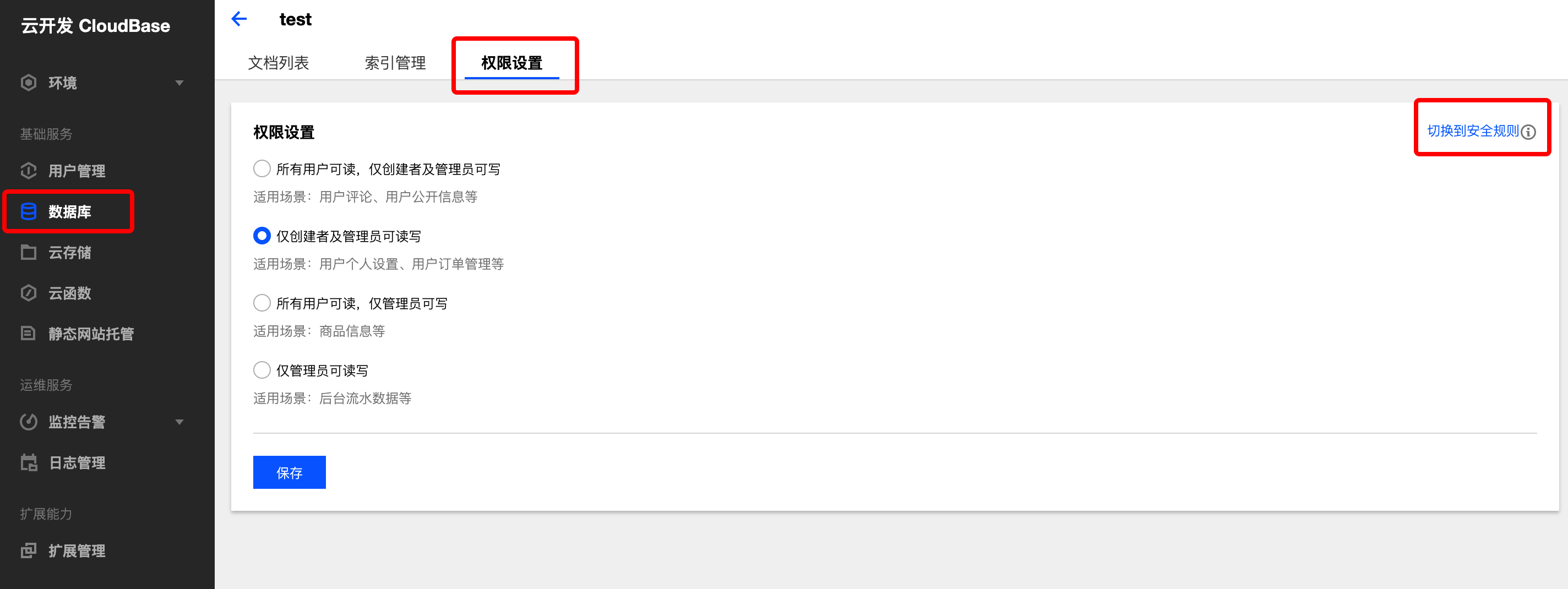
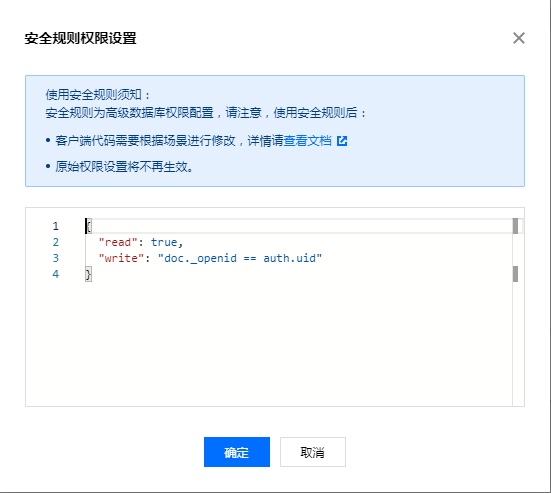
- Select to switch to Security Rules. The system converts the existing basic permissions into corresponding security rules, and developers can also modify them based on that.
- The security rules have been successfully set up. You can subsequently view and modify the security rules in use within the permission settings.
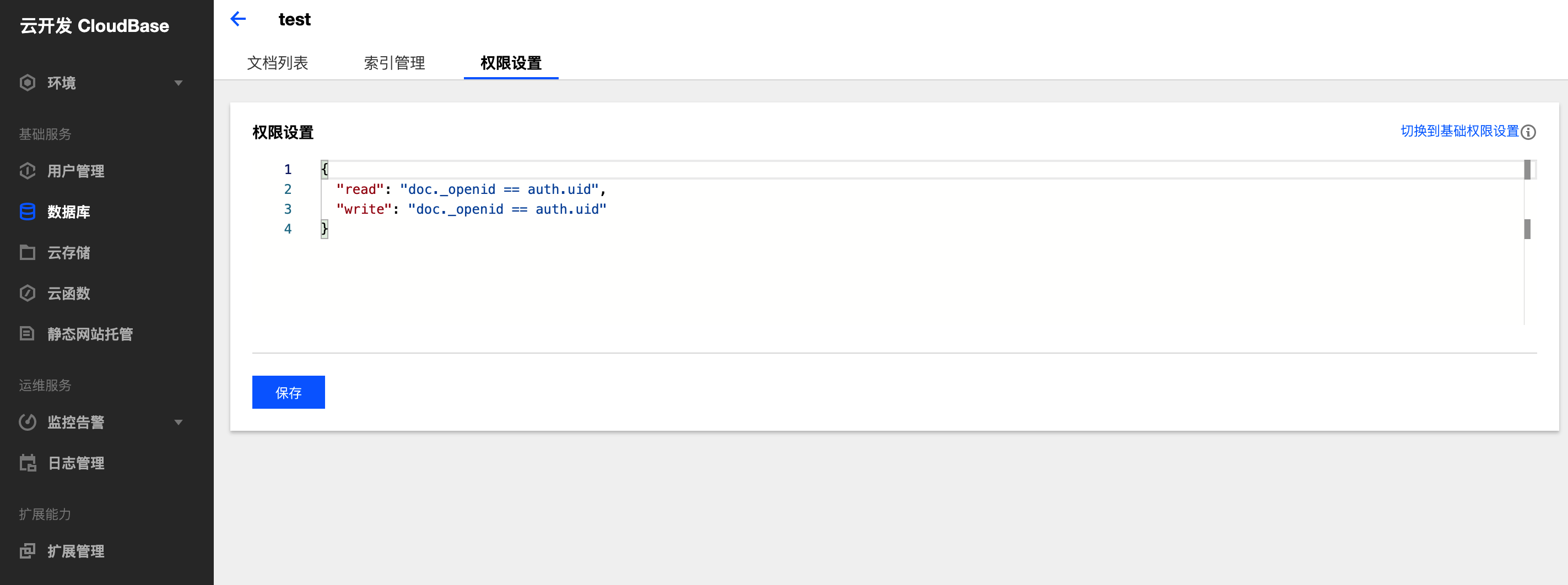
3. Editing and Publishing Security Rules
In the Permission Control page of the Cloud Development Console, you can edit the required security rules. For example, in the aforementioned forum application scenario, you can modify the permissions of the posts collection to the following rules:
{
"read": "auth != null", // All logged-in users can read
"create": "auth != null", // All logged-in users can create posts
"update": "doc.userID == auth.openid", // Users can only modify their own posts
"delete": "doc.userID == auth.openid" // Users can only delete their own posts
}
通过保存按鈕使编辑的新规则部署云端,保存成功后安全规则即时生效。