API Key Configuration
Overview
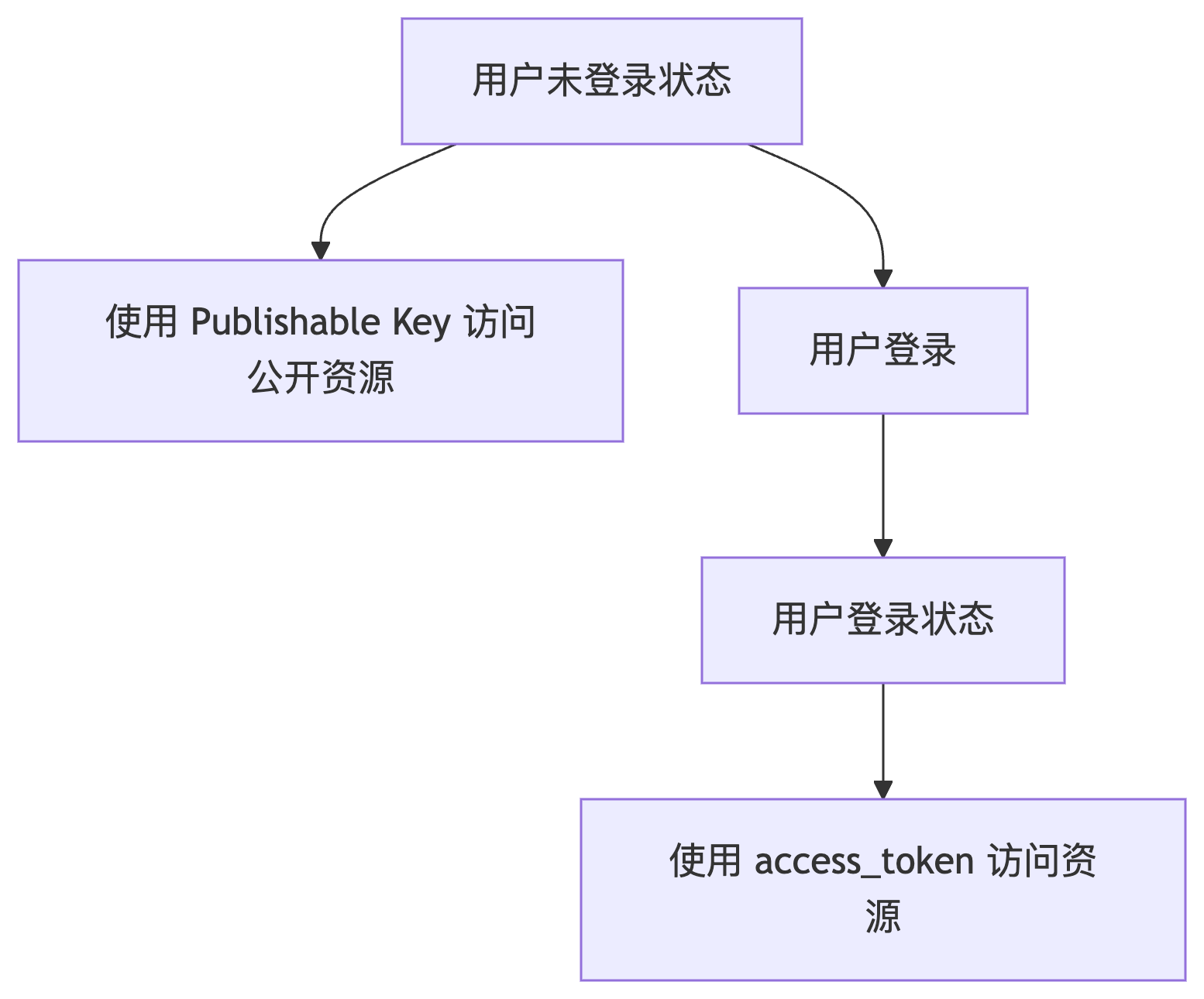
API Key is the core authentication credential for Tencent Cloud TCB, used to control resource access permissions and determine which resources can be accessed (such as HTTP APIs, Cloud Functions, Cloud Run, etc.)
Resource access can be directly performed via API Key without login authentication
API Key Types
API Key is used to authenticate resource access permissions, enabling applications to access Tencent Cloud's resource services, and is not intended for user differentiation. API Keys fall into the following two categories:
- Client-side Publishable Key
- Server-side API Key
- Applicable frameworks:
JS SDK,HTTP API - User Permissions: Anonymous User Permissions
- Validity Period: Permanent
- Obtaining Method: Obtain via TCB/ApiKey Management
💡 Note: Can be exposed in the browser, used to request publicly accessible resources, and can effectively reduce MAU.
Using Examples
See JS SDK Initialization for details:
const app = cloudbase.init({
env: "your-env-id",
accessKey: "<publishable_key>",
});
app.callFunction({
name: "test",
});
app.models.test.get();
- Applicable frameworks:
HTTP API - User Permissions: Administrator Permissions
- Validity Period: Permanent
- Obtaining Method: Obtain via TCB/ApiKey Management
⚠️ Note: Tokens are key credentials for identity authentication. Keep them secure. ApiKey must never be used on the client side.
Using Examples
See HTTP API Authentication for details:
curl -X POST \
https://tcb-api.tencentcloudapi.com/web \
-H 'Content-Type: application/json' \
-H 'Authorization: Bearer <apikey>' \
-d '{
"action": "functions.invoke",
"function_name": "test",
"request_data": {}
}'
Publishable Key and Login Authentication
Using a Publishable Key does not mean that the default guest identity has been adopted for login. It merely employs a publicly accessible key for resource access and does not carry any user information.
In applications, you can use a Publishable Key to access Tencent Cloud resources. Users can also access resources using their personal access_token via Login Authentication. These two approaches are not mutually exclusive.